Emily Mossburg - Three warnings. Two cyber threats. One mandate. Zero Trust.
Embrace Cybersecurity: Zero Trust Must Start Today
The modern enterprise environment poses new challenges for organizations - the quest to secure digital spaces. This transition isn't effortless or rapid. The change, however, presents an effective frame to secure new realities such as remote work environments and digital transformation initiatives. That frame is known as Zero Trust, a cornerstone of today's cybersecurity measures.
Understanding the Threat Landscape
Firstly, the digital threat landscape is expanding at an accelerated rate, further necessitated by instances such as the ransomware attack on the Colonial Pipeline and the cyber assault on the Irish National Health System. These attacks have impacted numerous entities, big and small, revealing an alarming reality: global businesses are expected to face a ransomware attack every 11 seconds, costing up to $20 billion in 2020.
The Shift to Remote Work
The shift to remote work over the last 18 months has profoundly impacted all organizations - quite dramatically - with 64% of the organizations planning a physical return in some fashion in 2021. Hence, different work environments signify diverse cyber attack surfaces.
Why Organizations Need to Embed Cybersecurity into their Strategic Plans
Moreover, in a constantly evolving technological space, companies must shift their approach to doing business. With increasing digital interconnectedness, cyber risks potentially surge. As a result, it's imperative for organizations to consider cybersecurity from the get-go, making it an integral part of the innovation life cycle and digital transformation initiatives. This is possible through embracing and implementing the zero trust model.
Zero Trust: What Is It?
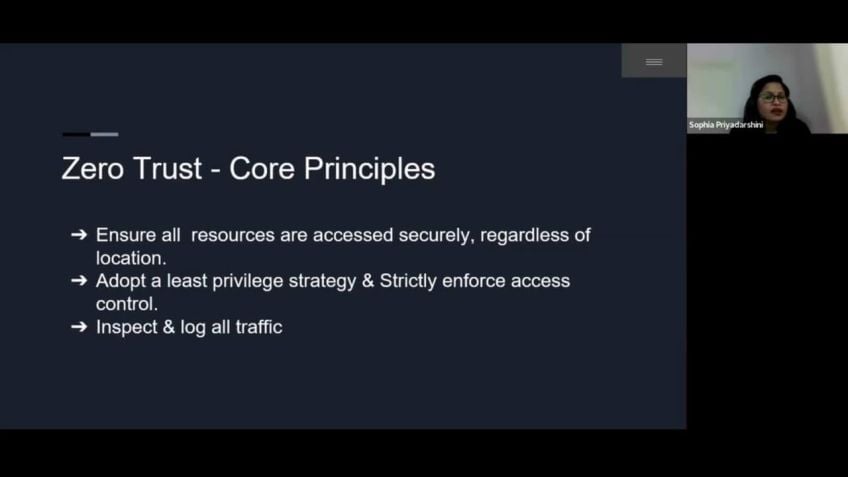
Zero Trust is an enterprise security model where no person, device, application, or system is trusted by default. It implies more than just a technical shift—it represents a cultural shift for organizations. In essence, the model promotes the principle of least privilege by providing individuals and entities with only the access they need.
Implementing Zero Trust: A Dual Approach
Implementing Zero Trust model requires a technical and an organizational approach. On a technical level, it is built on five foundational capabilities: identities, workloads, data, networks, and devices. From an organizational standpoint, factors such as culture and architecture governance, operations, and policies need to be taken into account.
Towards a Secure Future: Embracing Zero Trust
To drive the transformation towards Zero Trust, organizations need a roadmap, showing the business's benefits to fully secure buy-in. Transitioning may seem daunting as it can affect roles within cybersecurity teams. Hence, clear communication about the changes and clarity over the committed skill set plays a vital role in the journey towards Zero Trust.
Addressing Cyber Basics
As a security measure, patches need to be applied automatically and devices having outdated patches should be quarantined. As employees return to the workplaces, organizations need to assess systems for security gaps, track the location of critical assets, and understand business requirements. The important aspect here is not to get paralyzed by analysis.
Conclusion
In conclusion, the adoption of Zero Trust signals a proactive approach to cyber defense and enables security to move from a restrictive stance to a more enabling approach. This makes cybersecurity an integral part of business functioning, essentially, transforming it into a business enabler. Now is the time to focus on embedding cybersecurity into strategic plans and move fast with Zero Trust as your guiding light. After all, in this digital age, a zero-trust approach may be the only path to true security.
Video Transcription
Thank you so much. And I'm really excited to be here. Why don't we go ahead and jump into the presentation today? We're gonna chat about a conceptual framework that helps organizations secure our modern, modern enterprise environments.And and the changes in this approach aren't things that come easily and they're not quick switches for an organization, but this is an effective frame for securing the new realities that we're living with today. And that includes the remote work environment as well as the various ongoing and continuous digital transformation initiatives that we're all seeing as part of our organizations. And that really leads us to one thing and that's zero trust. Uh Moving on. I wanna start by just level setting.
First, threats are speeding up and they're becoming even more prevalent just days after the ransomware attack on colonial pipeline triggered the jet fuel shortages and the gasoline shortages and panic buying that we all were part of, there was a different group of cyber criminals and they held the Irish National Health System hostage with ransomware.
And in just the past couple of weeks, more organizations have been hit and this ranges from the city of the University of New York to the Massachusetts Steamship Authority and that runs the ferries from Martha's Martha's Vineyard to Nantucket in including a minor league baseball team, uh the Birmingham Barons.
So we're seeing all kinds of targets as it relates to cyber attacks. And global businesses are expected to face a ransomware attack every 11 seconds and that's gonna cost us $20 billion in, in us currency in 2020. The type of attacks are not new and but the number of adversaries and the number of attacks continue to increase and the targets as I mentioned are of all sizes in all locations and all industries. And if there was ever a time for us and for organizations to focus on embedding cyber into strategic plans, priorities and initiatives, it was probably yesterday, but we're gonna have to make today work too. If you wanna go ahead and and forward on the shift to remote work has definitely been felt by all of us over the last 18 months. And many organizations had no choice but to ask their employees to leverage their company issued laptops or even their own personal devices to work from home during the time where we were all ordered to stay at home. Uh The workforce proved that in many cases, we we could all be productive if not even more productive than when we were in the office.
And we actually did a survey Deloitte, did a survey in April of this year asking our clients how they were approaching the return to the workplace. And what we saw was there's no permanent shift to working from home all the time as the new normal and 67% of the organizations we surveyed remain fully remote today, but 64% are planning a physical return of some sort in some fashion in 2021. So I think that what this means is that we're gonna continue to see different ways in which we're working, which means different environments and a different attack surface as it relates to cyber. If we wanna go ahead and push forward to the next slide, digital transformation has really become the new norm. Um There's transformation happening and evolution happening and new types of technology being rolled out all the time consistently. If there's any new consistency, it's this change in this evolution of technology that's happening all the time. And with that, you know, companies are really focused on driving more success, more engagement with their customers, new ways of doing businesses. But as technology is changing and as companies change the way that they do business, we become more interconnected, we become more complex in terms of the technologies that we're using.
And with the advent of all these new possibilities and the new connectivity, the amount of cyber risk that we're all experiencing and potentially um is around the corner continues to increase. And and what we're truly seeing today is that organizations can no longer think about security.
After the fact, security can't be an afterthought. Cyber has to be embedded from the very beginning of the innovation life cycle and any digital transformation efforts, it needs to basically be included as an enabler of success. And and when an organization gets this right, then they can really make sure that they can transact and do business in a safe and secure and successful manner. And this is really where zero trust can help. So, you know, what is zero trust, zero trust is an enterprise security model. Um And in this model, no people, no devices, no applications and or systems are trusted by default. And it's a, it's a concept that we've been talking about for for many years. But it's one that continues to evolve in terms of being adopted and it's really more than a a shift of technology. It's a cultural shift that organizations have to go through as well. And if we think about recent um high profile cybersecurity events such as solar winds where it was a trusted um system or I'm sorry, a trusted piece of software within the organization, it really brings zero trust to the forefront and many organizations are trying to figure out, you know, how can we stop thinking about zero trust conceptually and how can we actually implement it within our organizations?
And you know, so what's fueling this interest? What's fueling the excitement about zero trust and it's really the need for business agility, the need to drive fast nimble digital transformation as everything is connected to everything, we're seeing a huge increase in the connectivity and the collaboration and that's fantastic.
And the zero trust model can support the transformation, it can support this digital uh business and it can also reduce cost especially when it comes to regulatory compliance and um things like mergers and acquisitions particularly where there's a lot of amount of integration work that has to be done.
And I think these are some of the real reasons that there's so much interest in zero trust. So let's get into a little bit more of the specifics of what zero trust entails. And you know, if we think about it at the most basic level, it's a conceptual framework for securing it environment. Um as we all know and have talked about is no network perimeter anymore. And the reality of today is organizations, you know, can't set up the same kind of defenses around their or their company in order to keep the bad guys out. I instead uh the modern business processes of today and digital transformations have created a very complex and interconnected set of it ecosystems. And so the perimeter model where you distrust anyone outside the perimeter and trust everyone inside the perimeter, it doesn't work anymore and it no longer applies because as we just talked about, there is no perimeter. And so the zero trust model takes a risk based approach and it really focuses on least privileged access and it's least privileged access over all systems, all applications and all data.
Basically, nobody is implicitly trusted and, and people and devices and machines are only given access that they absolutely need and no more. A and what this means at the business level is zero trust can be dynamic and responsive to cyber risks um in a way that the old perimeter methods couldn't be. And this allows um cybersecurity within an organization to be able to be more responsive to the needs of the business. If you think about this, from a technical perspective, it's really built on five foundational capabilities within cyber identities, workloads data networks and devices and in a zero trust framework. This is represented by telemetry, analytics, orchestration and automation of technologies across these foundational capabilities.
But I think what's equally as important is the fact that beyond the technical architecture, we have to look at the softer side of implementing zero trust, there's really a component and an element of organizational change that we need to consider. And what, what are those domains of or organizational change that we need to keep in mind? One is culture and organization. I mean, zero trust is going to be driven over time and there's going to need to be a fundamental shift in the culture of the organization. If you think about the the architectural governance and governance is really the key word in all of this. You've got to think about how this architecture is gonna be maintained over time. And you're gonna need to basically be able to govern that architecture over time. And you're gonna need the team that's available to do that from an operation standpoint, there's key changes to operations and that's gonna have to be planned for from an organizational standpoint. And, and last but not least is the policy component which is really at the heart of everything.
If no person, no machine, no device is trusted by default, how will company policies need to change in order to make sure that work is done safely and effectively and all of these capabilities and all of these pieces of organizational change cut across the organization itself.
And that's when, when, why, when we think about zero trust, we have to think not only about the technical side but this softer organizational side as well. And, and the the bottom line is you can't go out and buy zero trust. It's not a technology, it's not a solution, it's a methodology and that th that methodology benefits the entirety of the organization. And it's really important to make sure to get the support of the organization overall to drive this transformation. And to do this, you really need a road map that shows the business benefits so that you can get the right level of buy it. And you also need to think about the cybersecurity organization. Um We've all spent years building perimeters and defending them and, and now we're going to a new model and people are worried that it's all going to change. Um, and that can be scary and that can be frightening. And so it's important to communicate to people on your cybersecurity teams. How this transition to zero trust is gonna change their roles, the organization, their training, et cetera, adoption of zero trust does demand a shift in skill set. And in order for this to be done in a meaningful way, there's a transformational commitment that needs to be made across relevant stakeholders and that includes the budget to drive this transformation. And it's also important to consider people process and the implications of this journey towards zero trust.
So taking into consideration aspects such as the end user training or organizational change management processes and incident management if we move forward. So what does this mean in terms of a cyber basics and what can be more basic in the world of cyber than patching? And it professionals often think of the term cyber security posture as referring to an organization's overall security environment in hybrid work environments. Patches need to be applied automatically and they need to be applied to remote work devices as well as those devices within the organization and within the infrastructure. And if a single laptop patches or a single devices like patches are out of date. That device needs to be quarantined.
And so what you're basically saying in that in that is that you, that device can only access the update server at that point in time. And once that update takes place, the rest of the network can then be accessed as needed further to the other to end points, to strengthen security posture. As we invite employees back to the workplaces, organizations need to assess their systems for security gaps and we need to be able to track the location of critical assets and understand what business requirements exist. The thing to avoid in all of this is paralysis by analysis.
Uh A lot of organizations don't really know what zero trust means and they think that it may be some gigantic rip and replace undertaking and that's not what we're talking about. We're talking about helping clients to understand the environments and the devices that they need to protect, to look at their existing cyber capabilities and to understand the gaps as it relates to zero trust. And there's often considerations as to where to start some organizations, it's best to start with the global crown jewels or the crown jewels that are most important to that organization. And in some cases, it's important to start with low hanging, lower risk priorities. In any case, any transformation can cause disruption. And ultimately, you wanna start your journey by disrupting as few critical business processes as possible. Moving on. We've seen some really interesting use cases related to zero trust. And one is the desire of organizations to expand into high risk geographies.
They, they want, want ways to segment different parts of their business so that they can hit a kill switch. If there's a security breach, they wanna prevent threat actors from being able to move laterally across the network. And, and so that's been another component of zero trust as it relates to segmentation and being able to enable that kill switch. Um We've also seen interesting movement as it relates to VPN technologies and the way in which remote users access your organization, VPN technologies were not originally designed to incorporate concepts such as conditional access device, interrogation, least privilege. And we've seen a, a lot of organizations move towards technologies such as secure edges, secure access service edge sassy. Um And that's being adopted by organizations to really drive more remote access capabilities and be able to be more granular in terms of their access controls.
Why don't we go ahead and, and push forward at the end of the day, aligning to zero trust signals organizational commitment and it signals organizational commitment to a more proactive approach to cyber defense. Um And that's really another driver considering the prevalence of remote work by integrating security controls, organizations can automate enrichment and response actions in order to en enhance efficiency of security operations and that reduces the overall dwell time of potential.
Uh bad guys, adversaries and, and potential breaches within an environment, repetitive and manual tasks can be automated and proactive action to isolate and remediate. Uh security threats can be orchestrated and that's through integrated controls. So let me give you an example, if a remote user's account is expect is compromised, automated actions can be taken and they they can be taken to disconnect but also to disable the users access in near real time. So in conclusion, zero trust enables security to move away from the stance of you can't do that to truly enabling the business with. We can't do that and we can do it securely and it makes cyber integral to how businesses work. And that's what's really exciting to me is to turn this into a business in a station enabler. And that's what zero trust allows us to do with that. I'm gonna go ahead the session. So thank you all so very much for joining us and uh hopefully you've enjoyed it. Thank you.